An Interesting Reading on Honest Security
An interesting reading I came across called Honest Security by Jason Meller.

A while back I had applied for a Senior Security Engineer role at a company called Maven Clinic. As I read the job description, I came across the following that caught my attention:
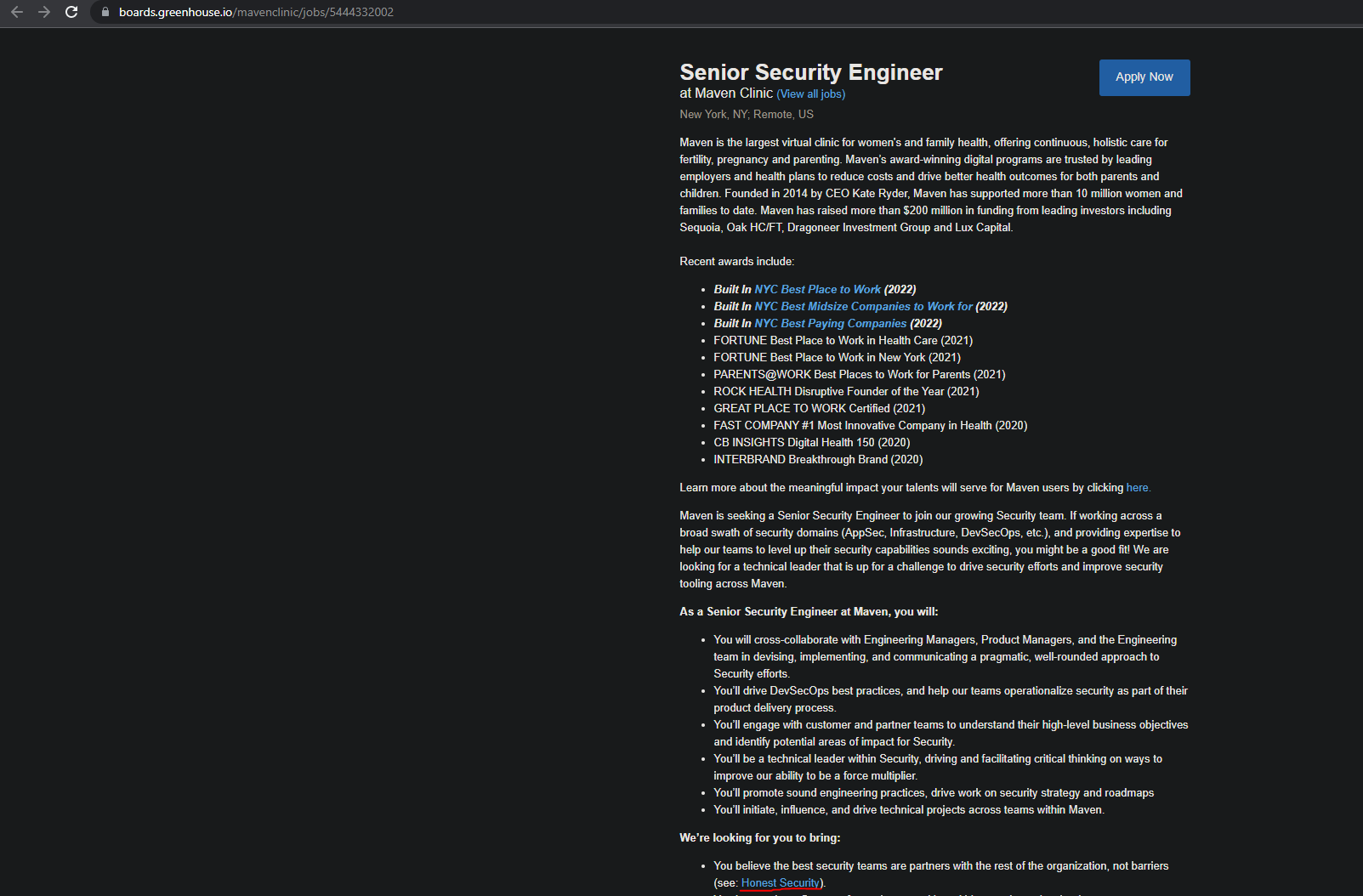
What caught my attention was the highlighted text Honest Security. Before we get into what honest security is, the provided description explains it well. It says, "You believe the best security teams are partners with the rest of the organization, not barriers." This caught my attention because as someone who is searching for their next opportunity, I try my best to look beyond what a company can offer me. What do I mean by this? I am saying that I want to get an idea of it's culture and how the specific role I had applied, directly impacts that culture. If a security team is being big brother type not respecting end users privacy, and are not empathetic with them, then one can say that such team is a barrier to the rest of the organization because this is unethical and will lead to your end users not trusting you creating an unhealthy working relationship with them. Of course there can be so many other examples out there where a security team can be a barrier to the rest of the organization. What I am trying to get at is that for a company to have posted this in their job description and even provided background information about what honest security is, it helped me to better understand not only what this concept is, but also tells me that such company cares about this because they included it in their job description for a reason. It helped me to better understand the impact that the role can have on the culture of the company to ensure candidates are aligned with this culture. Now with that out of the way, let's get into what honest security is!
What is Honest Security?
Honest Security is described as "one part guide and another-part manifesto that defines a user-first approach to security and IT compliance." The guide was written by Jason Meller with a lot of help from others. He is the Co-Founder and CEO of Kolide, "a startup that helps organizations implement the principles found in this guide through a beautifully designed Slack app." When I had first clicked on and visited the provided link to Honest Security's guide, I didn't read the entire guide. I saw there was a downloadable PDF which I downloaded to my computer. I had read the tenets of honest security which to me was a great way to quickly introduce the reader to how the rest of the guide was going to present itself. It was the first thing that caught my attention because each tenet resonated with my values and had put me in a good mood. I was happy to learn that someone out there had taken the time to create this guide that not only resonated with my values, but was tackling several challenges in a very elegant way and sharing it with the rest of the world! The one tenet that stood out to me the most, was the very first tenet that says, "The values your organization stands behind should be well-represented in your security program". This tenet stood out to me the most because it's something that can be very difficult to achieve from organization to organization. For example, not every organization may have a security team. Some may have a security team but they are located in other parts of the world where different values may clash that are not close to the values of the organization. Lastly is how and who creates the values and supports them at the org in the first place? Just the CEO? Or is it both HR and CEO and nobody else? Are such values just used as a means to look good in front of an audience? All of this comes to my mind because it adds complexity to what the first tenet wishes to address. It certainly takes a team effort to successfully be able to adapt such tenet because there needs to be alignment with everyone involved in this process. From the lowest person on the totem pole to the owner or CEO of the organization. If I were an owner of a company and wish to incorporate the first tenet, I would need to be honest with myself by verifying everything I do and say is indeed representative of the values of the company. There is no other way or a shortcut. To me this is how an owner or CEO should approach to incorporate the first tenet. Figuring out how you present yourself and the company to everyone can be the difference between adapting the first tenet, to not adapting it at all. To end this section, if an organization is not aligned with their own values, then much less will a security team be able to adapt such values in their security program. This is why security is said to be a team sport, which is reflective in what honest security really is. It's about making security a part of your culture!
Reading Honest Security Two Months Later
It was two months later that I took the time to read Honest Security in its entirety. As someone who previously worked in an IT team, and provided cross functional support, as I continued to read I found myself reflecting on my past experiences working for different companies. For example, at a recent experience I had the opportunity to onboard a mobile device management (MDM) software called Workspace ONE UEM by VMware. It's a unified endpoint management or in simpler terms a device management software that allows administrators to manage a device. The whole reason why this software was onboarded was because not only there was a security incident that occurred where a laptop was lost/stolen and nobody knew if the disk was encrypted, but also the company wanted to become ISO 27001 certified, and to remain compliant with this information security standard, having such software on end users devices is a requirement. I remember very well the first email that was sent out from the VP of infrastructure. Some points touched were automatic updates, disk encryption, screen lock, locate lost/stolen device, remote wipe device, and lastly that this initiative was a requirement as part of the company's efforts to become ISO 27001 certified. What happened later was something that could annoy a few but to me I felt that people were doing the right thing. When we began to send out generated emails with download links to enroll devices, many of the more tech savvy users, mainly those in R&D whom we had tested the deployment on first, had reached out to the VP of infrastructure about concerns mainly due to privacy. For example, many had asked if such software was going to monitor them and many were concerned mainly about disruption of their workflow. I found that the entire process did not go as smooth for several reasons:
- The deployment was tested on the main fleet of endpoint devices which were Windows and Mac, however we did not take into account a fundamental aspect of honest security and that is the second tenet that says, "A positive working relationship between the end-user and the security team is incredibly valuable and worth fostering."
- When someone is drafting an initial email on deploying an MDM software of such kind to an entire department and much later to the entire company, you need to be very CAREFUL on what words you use and how you explain that such software is only there to make the company successful.
- I'm not saying that the email that was sent out was poor by any means, but upon reading honest security, to me I felt enlightened about how important it is to provide not only transparency but be prepared to have people provide feedback and depending on how you absorb that feedback, can say a lot about the relationship you have with your end users!
- Lastly, instead of using the word "requirement" which I am one of those people that used it a lot to explain to end users why such software was needed and would just end there, it's important to understand that not everyone will view it as you do. This is why taking the time educating end users is crucial because when we inform people about how to use such software and seek help when needed, they are informed and motivated to continue to work with you which is a win-win solution. This together addresses both tenets 2 and 5 respectively, "A positive working relationship between the end-user and the security team is incredibly valuable and worth fostering" and "End-users are capable of making rational and informed decisions about security risks when educated and honestly motivated".
Incorporating Honest Security for the Future
As I search for my next opportunity, not only do I want to incorporate the values in the guide, but also be able to share such a guide with others. I hope to connect with more people one day who wish to tackle security challenges differently so I can not only continue growing, but also remind myself that the world is much bigger and the path ahead is much more brighter as I continue to come across like minded people who share similar values with me. :)
