The Snowball Effect of Supply Chain Attacks

Supply chain attacks are an escalating high impact threat that hit hard due to the interconnected nature of the modern software development ecosystem. The high level of trust placed in open-source components allows for these attacks to happen. We saw two recent large supply chain attacks from npm and Salesloft Drift. We'll go over these two attacks in detail, and learn the snowball effect it caused on an already fragile open-source ecosystem.
Attack of The Shai-Hulud Worm

The npm supply chain attack started off by the "s1ngularity/Nx" attack caused by what would be known as the Shai/Hulud worm. To get a better understanding, we need to know the timeline of everything that had happened prior.
Timeline
August 26, 2025: "The Shai-Hulud attack is believed to be a direct consequence of a previous incident where an attacker gained control of a maintainer's GitHub account and, in turn, stole their npm tokens. This initial breach, often referred to as the "s1ngularity/Nx" attack, established the initial foothold that was later leveraged to unleash the Shai-Hulud worm."
September 8, 2025: After the Nx compromise, a separate campaign that would be considered the largest npm hack in history begins that "injects cryptocurrency-stealing malware into 18 widely used npm packages with a combined 2.67 billion weekly downloads, including popular libraries like debug and chalk." It all started from a phishing email. One of the contributors of these two packages Josh Junon (Qix) npm account was compromised.
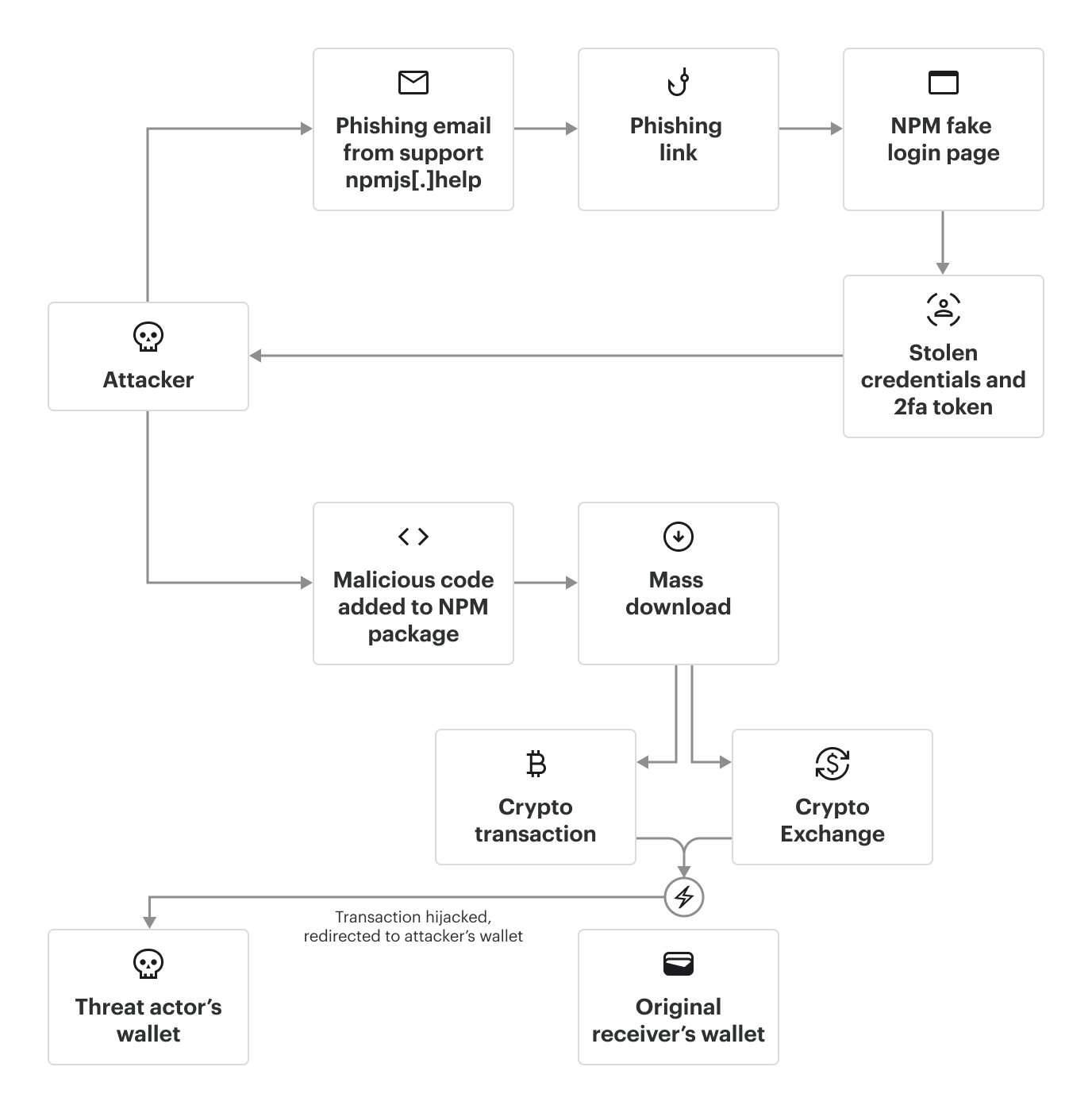
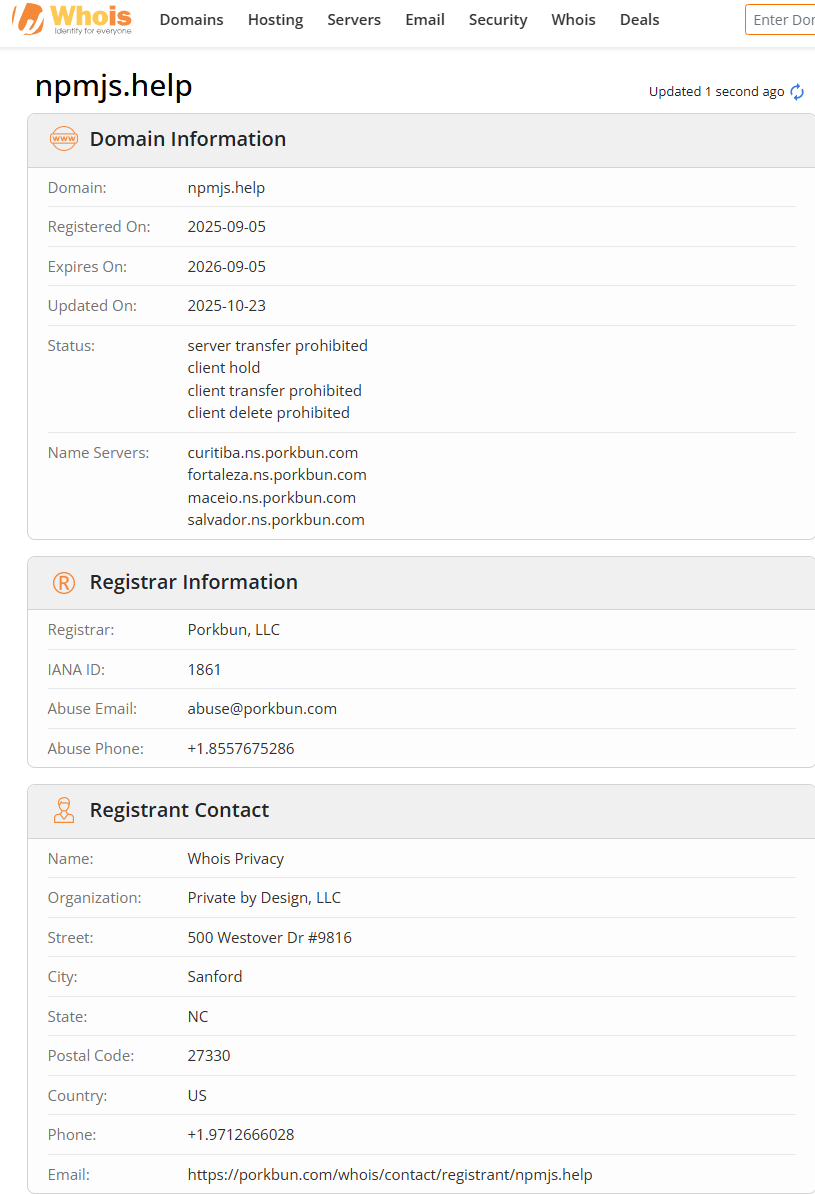

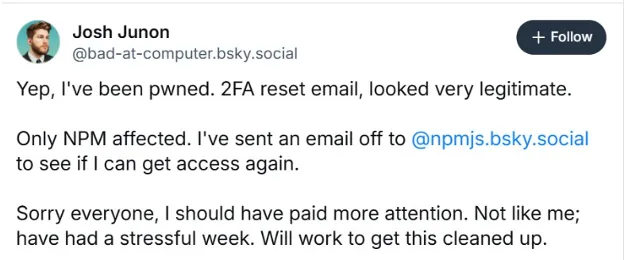
It is said that the "contact us" link in the email "actually linked to the legitimate npmjs.com contact us page, making it appear even more legit." Not much damage was done since the trojanized npm packages were only available for download for two hours; thus, the threat actors behind the attack were only able to generate $1,000 from their campaign. However, this attack had the potential to affect millions of developers and would serve as a prelude to the more sophisticated Shai-Hulud worm.
September 15, 2025: "On this day, hundreds of popular npm packages, such as ngx-bootstrap and @ctrl/tinycolor, are compromised with malicious code. The worm, dubbed Shai-Hulud (based on an artifact file named after the giant sandworm in the Dune series), is found to contain a postinstall script (bundle.js) that runs a self-replicating process. It steals credentials from the developer's machine, including npm tokens, GitHub Personal Access Tokens, and cloud service keys (AWS, GCP, Azure)."
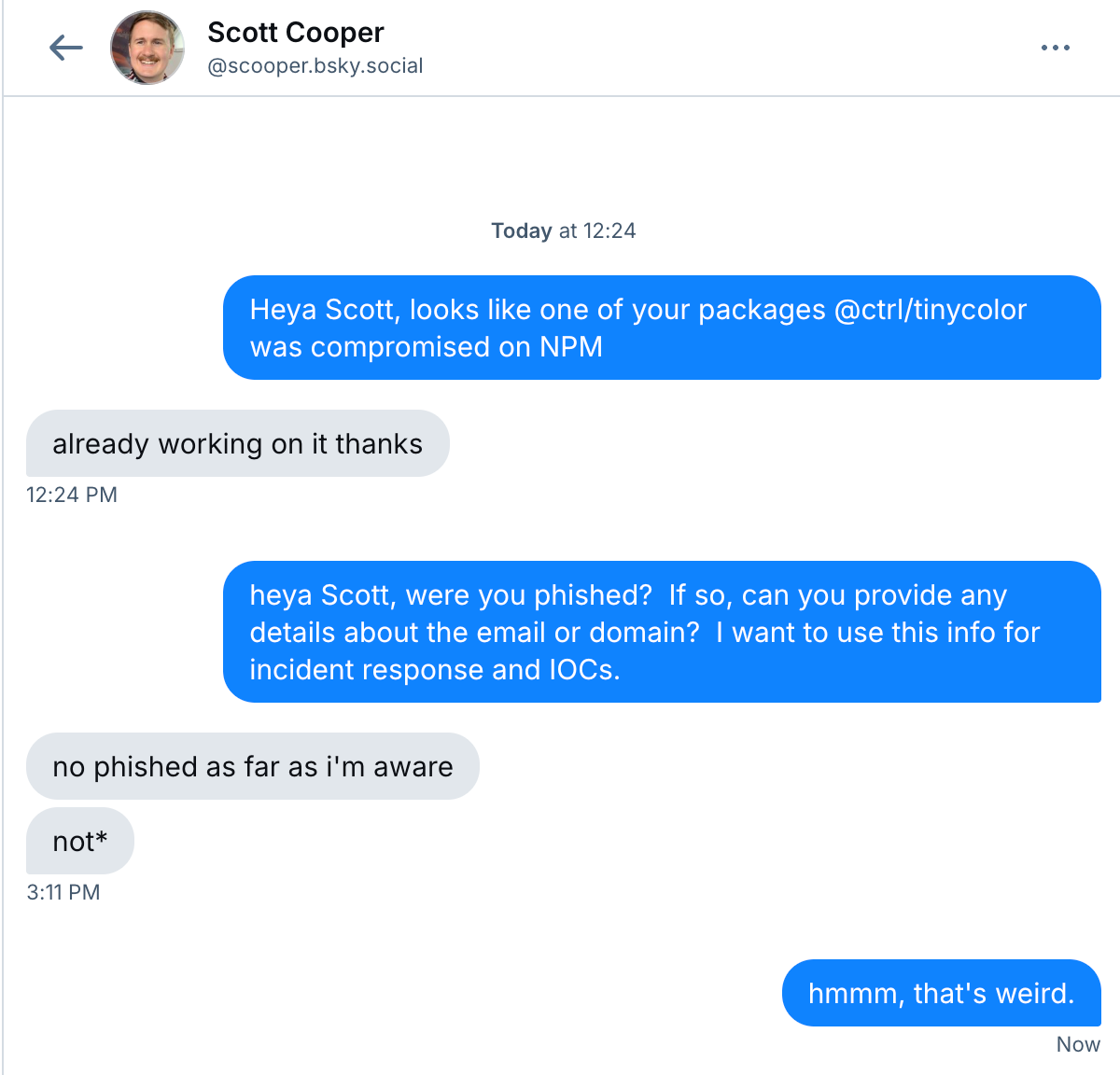
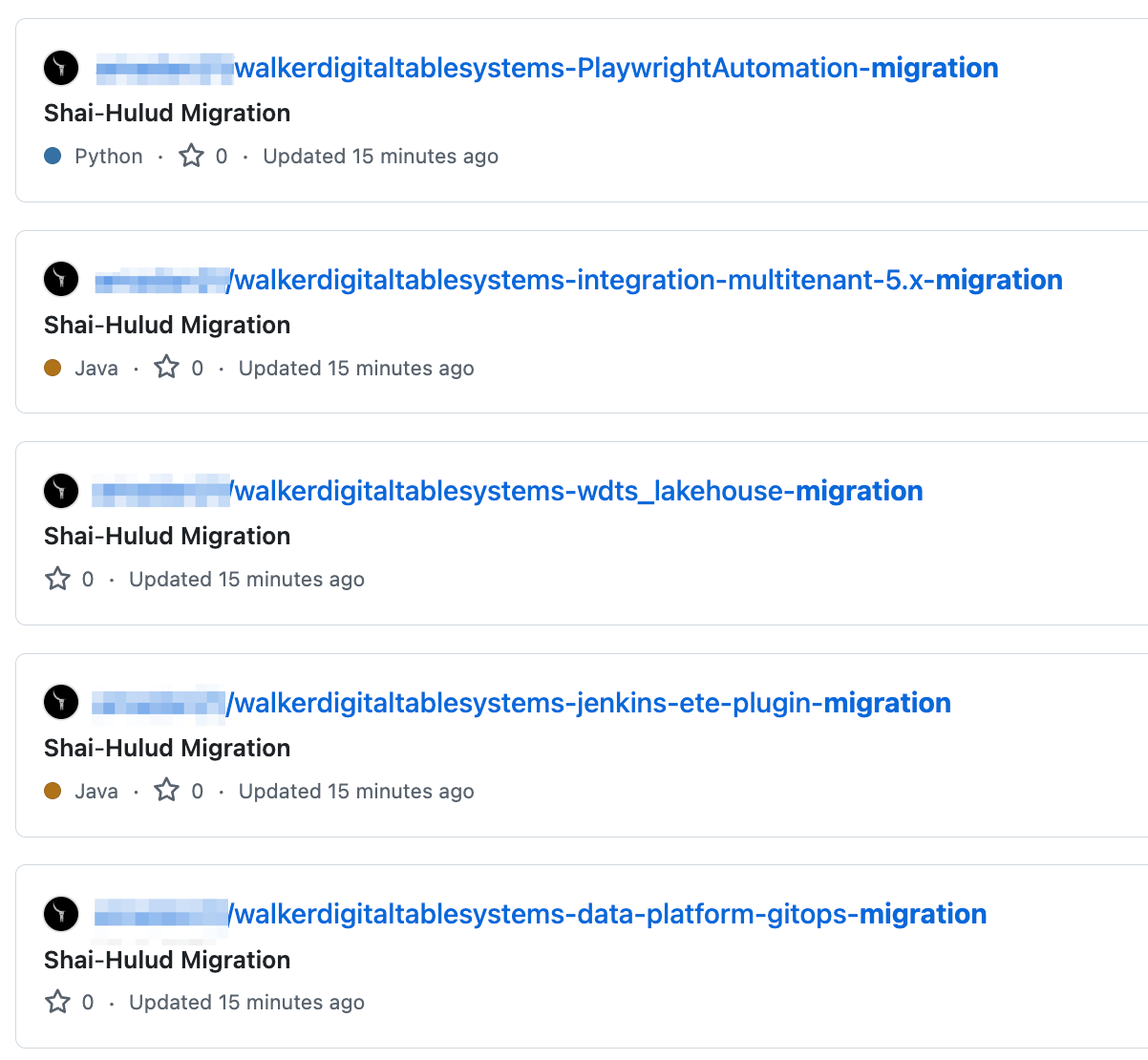
September 16, 2025: "Shai-Hulud's self-propagating mechanism begins to take hold, using the stolen npm tokens to compromise other packages maintained by the same developer. The malicious code is automatically injected into new versions of these packages, allowing the worm to spread rapidly across the npm ecosystem. The worm also begins exfiltrating stolen secrets in two primary ways:"
- By creating a public GitHub repository named "Shai-Hulud" on the victim's account and uploading a base64-encoded JSON file containing the harvested credentials.
- By injecting a malicious GitHub Actions workflow into accessible repositories, which exfiltrates secrets to an attacker-controlled webhook.
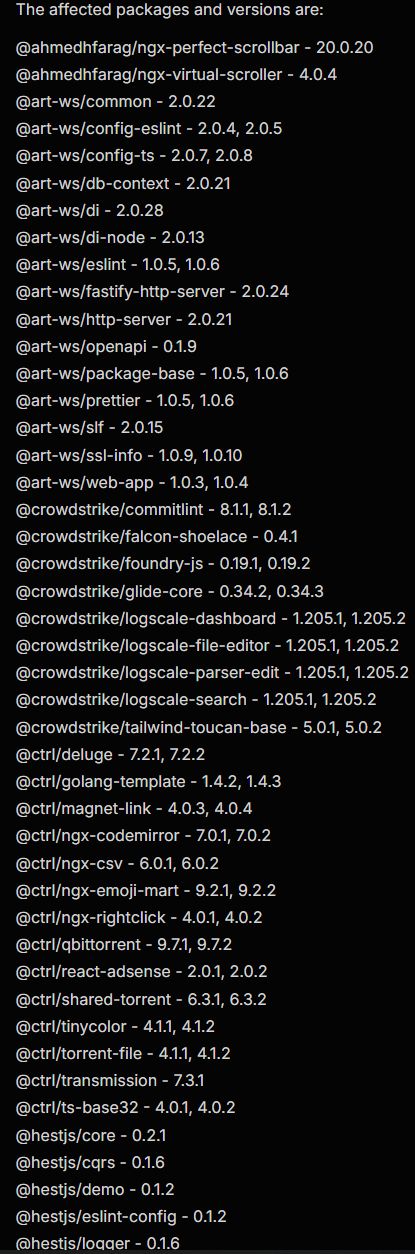
The quick response from the open-source community and security firms was crucial in mitigating the damage. Malicious packages were swiftly identified and removed from the npm registry. However, we can't ignore the fact how even CrowdStrike - one of the most security-conscious organizations was caught in the blast radius. It shows how deeply interconnected and fragile the open-source ecosystem can be.
Salesloft-Drift
The Salesloft-Drift integration was caused by an attacker gaining access to Salesloft's GitHub account. From there, "content was downloaded from multiple repositories, a guest user was added, and workflows were established to maintain their access. In addition to this, the attacker performed reconnaissance on both the Salesloft and Drift environments. A pivot was later done where the attacker leveraged their position to access Drift's AWS environment. OAuth tokens for Drift customers' technology integrations were stolen. Lastly, data exfiltration occurred where the attacker in possession of the stolen OAuth tokens, accessed customer data through the active Drift integrations."
Lessons Learned

The lessons learned are several. There is an urgent need in building resilience against future third-party supply chain attacks. The npm package compromise and the Salesloft-Drift OAuth supply chain attacks have demonstrated how attackers exploit trusted third parties to infiltrate organizations. The attackers didn't hack thousands of individual websites. They went "upstream" by compromising a single, trusted source - the maintainer's account. This had a snowball effect which triggered a larger series of cascading failures compromising countless systems that rely on that single piece of code. Organizations must prioritize defending against supply chain attacks. Some security best practices are below.
- Establishing C SCRM (SP 800 161) with board level oversight.
- Adopting SSDF (SP 800 218) in your CI/CD pipeline.
- Generate/Ingest SBOMs (anchore/syft) for every build.
- Layer SCA (dependencies) + SAST (first party code) + Secrets Scanning.
- Enforce Zero Trust (MFA/FIDO2, least privilege, microsegmentation, IdP hardening).
- Monitor & Drill Incident Response with supplier breach runbooks.
By implementing the above security best practices, resilience will be strengthened ensuring not only mitigation but also the response time in handling these attacks.
Ref: https://www.trellix.com/blogs/research/npm-account-hijacking-and-the-rise-of-supply-chain-attacks/
https://www.upguard.com/blog/salesloft-drift-breach
https://deepstrike.io/blog/supply-chain-attack-statistics-2025
