Why Threat Intelligence Matters

You may have heard countless times that the threat landscape is always growing. As cliche as it may sound, threats are prevalent because there will always be the potential for danger or a harmful event that can exploit a vulnerability and cause harm to a system, organization, or individual. This is why it's important to recognize the value that threat intelligence has in cybersecurity. What is threat intelligence? Gartner defines threat intelligence as, "evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard." In shorter words, threat intelligence helps people make better informed decisions about how to deter a threat. Now that we know what threat intelligence is, let's look at some examples of different types of threat intelligence.
Types of Threat Intelligence

We'll first cover the more simpler information to digest, and those are threat intelligence feeds. Just like there are news feeds on a journalism website or a feed on a social media platform that both show continual updates, a threat intelligence feed is a continually refreshed source of threat data. Such data includes indicators of compromise (IOC), suspicious domains, known malware signatures, and more. Below are some threat intelligence news feeds I use. I labeled them in order of skill level in understanding the material present, as some feeds present the user with more in depth information such as other related threats to reinforce the insight on the particular threat in question, charts and graphs, and protection mechanisms which may be unfamiliar to you:
- ZDNET Security. This site is very beginner friendly, and presents the user with practical solutions and tips and tricks in managing your cyber hygiene
- BleepingComputer. This site is also beginner friendly, similar to ZDNET Security, but presents more information on the actual threats. You will also see mentioned discounts and deals on various security related products like ZDNET Security does
- The Hacker News. Claims to be the #1 trusted cybersecurity news site. I included this site not because it is said to be #1, but it's a site that takes both what ZDNET Security and BleepingComputer have to offer, and provides more actionable insight on how to proactively identify and deter a threat. Another important mention worth mentioning is how many cybersecurity breaking news I have come across, have appeared first in The Hacker News site. For example, many other threat intelligence feeds often credit The Hacker News for first breaking the news. This site is more for those already familiar with various cybersecurity topics, and won't get lost in what is being presented to them
- Dark Reading. Another site that is more for those already familiar with various cybersecurity topics, Dark Reading presents the user with the perspectives of other security professionals, often articles written by CISOs. If you're interested in getting a really good understanding of how cybersecurity really functions at the enterprise level, then you've come to the right place! There is even a section dedicated to threat intelligence here.
- Recorded Future. Not for your everyday average internet user, Recorded Future specializes in threat intelligence, and is highly regarded for it. If you want to get the full breakdown of a threat, and be left with a firm grasp on next steps to take, you've come to the right place! This site presents highly advanced information, such as graphs and charts, as well as mentions from other threat intelligence feeds or other cybersecurity companies, and you will be prepared to plan out next steps in better managing your cyber hygiene!
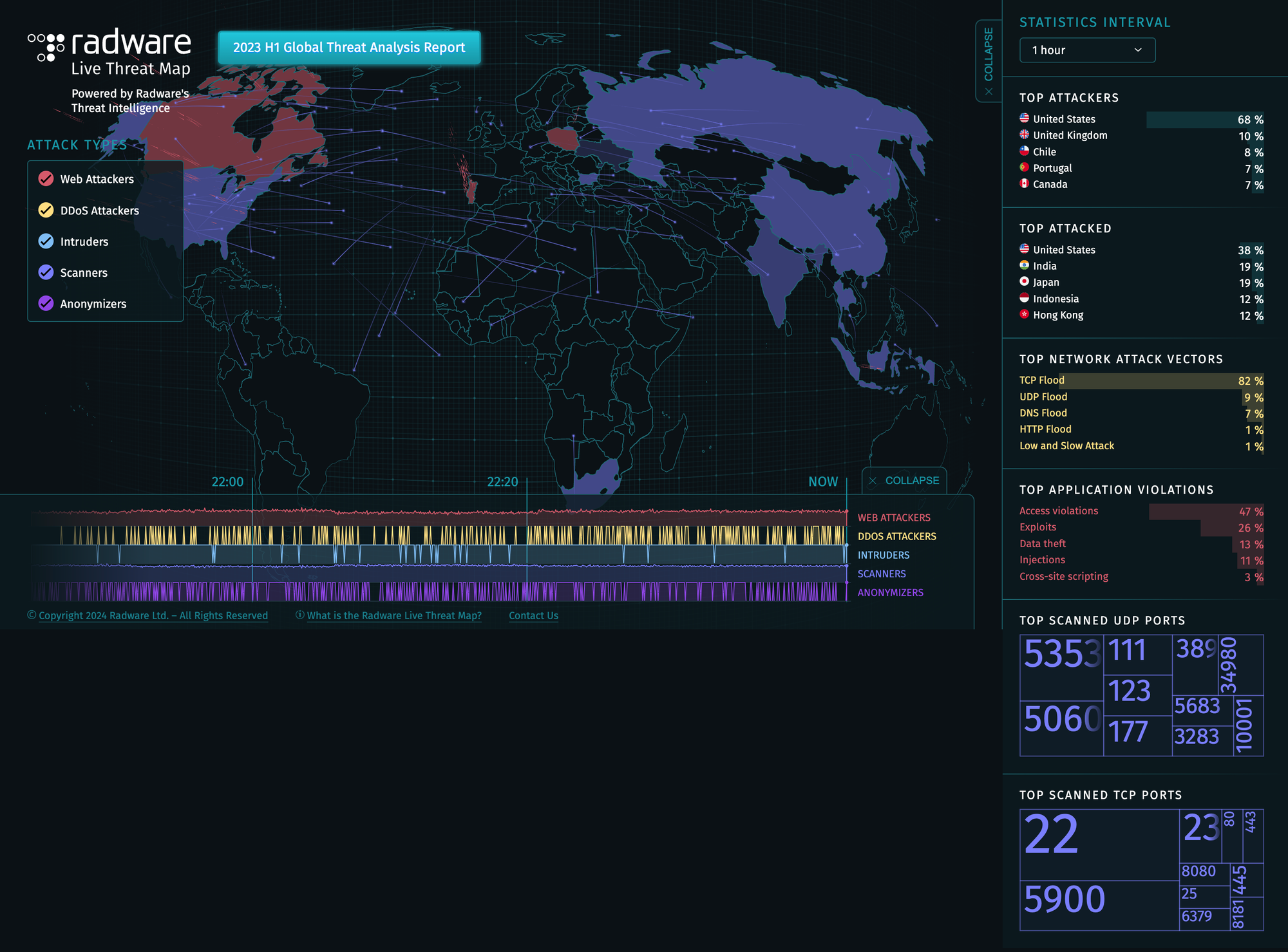
Now that we covered what are threat intelligence news feeds, there is also threat intelligence in the form of maps. These maps are called threat maps or cyber attack threat maps. Although this type of information would be overkill to show to someone just beginning to learn about cybersecurity, what is important to take away here is that these threat maps often provide a better picture of what are the most common types of threats that are occurring in a given time period. I personally do not use any threat map, but the reason I still included this information is because it is something that is not only useful, but helpful for those visual learners such as myself that want to see a clearer picture of things.
Lastly, there are tools like AbuseIPDB which are great in gathering more information on an IP or domain. You just enter in an IP or domain you wish to check whether it is malicious or abusive, and you will get a response on whether there are any reports of abuse. There is even a great feature called confidence of abuse, that gives you a percentage of how abuse the IP or domain is.
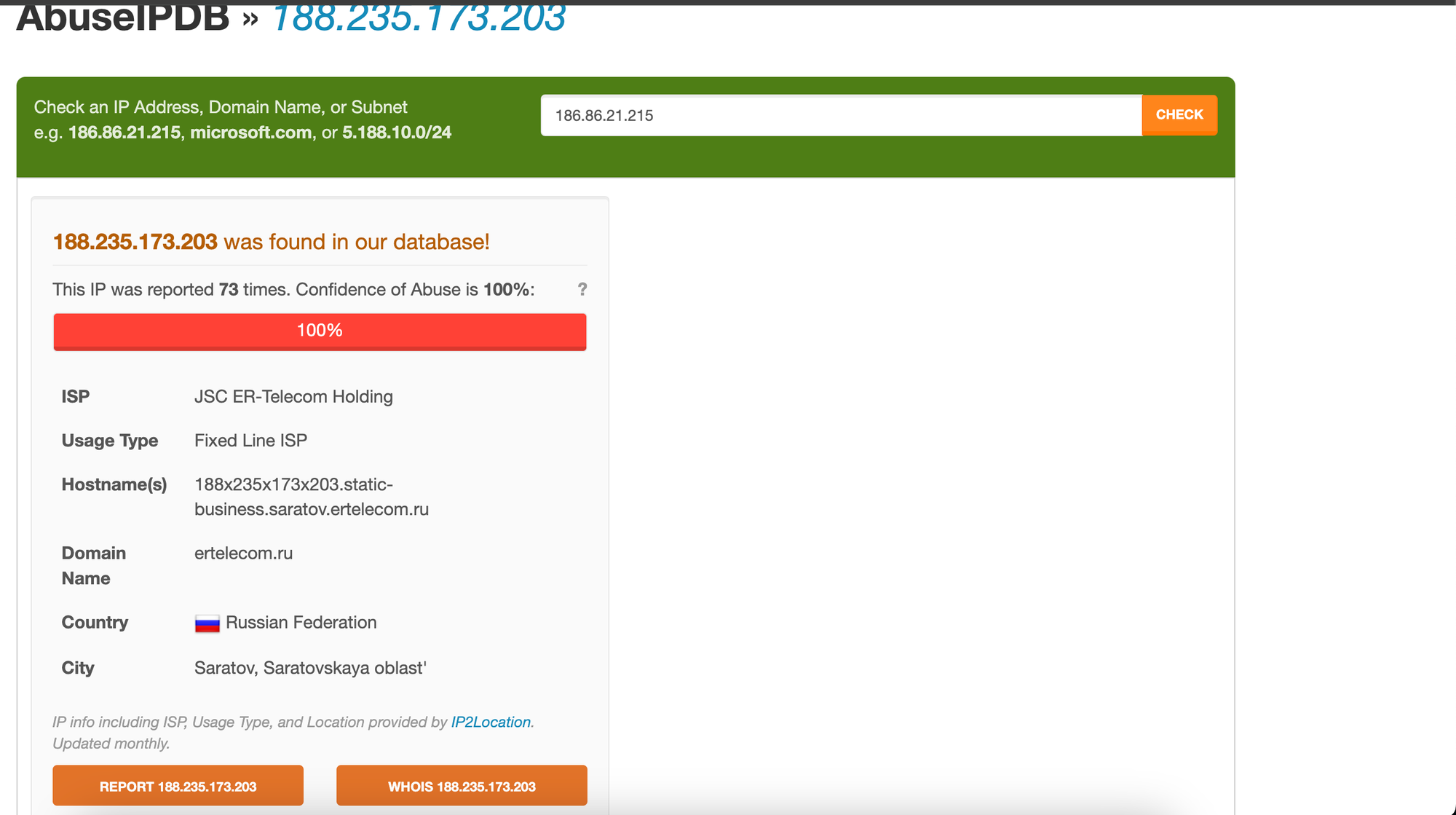
AbuseIPDB is a very powerful tool that has helped me in my career, specifically when doing log monitoring. I am able to see what threats are trying to come in, and what other potential threats that can be abused to affect the organization just by knowing the history of the abusive IP.
Towards a Better Informed Threat Landscape
Threat intelligence has evolved thankfully with the impact that social media has had on the digital world. It is often so easy now to see people posting on X discussing about a recent exploit or vulnerability. There are so many great resources in addition to the ones I mentioned, to familiarize yourself with how to stay vigilant and prepared to take action in the event one is affected by a threat. Recently, I had a great experience with a coworker where I shared some threat intelligence tools with them since they had unintentionally downloaded the wrong desktop application of a program they wanted to use.
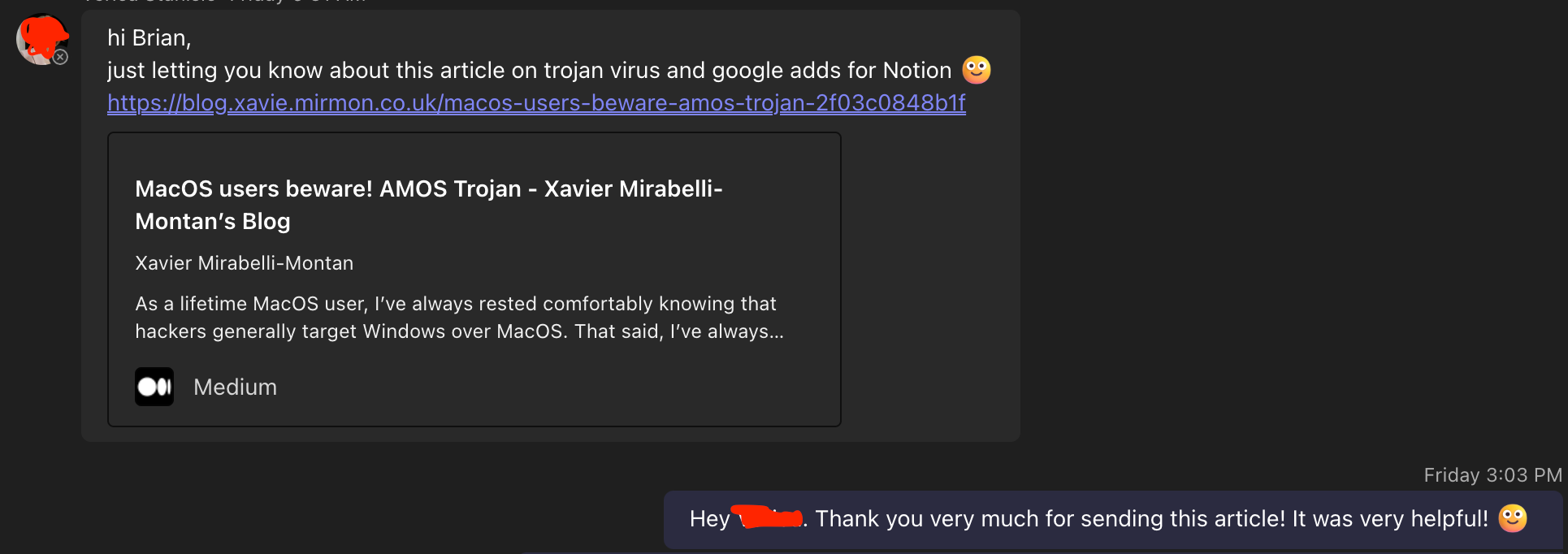
Long story short, the EDR software on the computer detected the site as malicious because of an indicator of compromise (IOC), the file that was unintentionally downloaded was malicious, so it was blocked from installing. Few days later, once I had handled the incident, the user shared with me a blog post from a user that also had downloaded the same malicious file. I was able to gather more details from reading the blog post, that the particular malware that was downloaded was a trojan. This is a great example of how threat intelligence can help people make better informed decisions on how to stay alert and proactively deter threats!
